How to hack
While looking for something else, I discovered that Google (of course) knows what people are trying to hack lately:
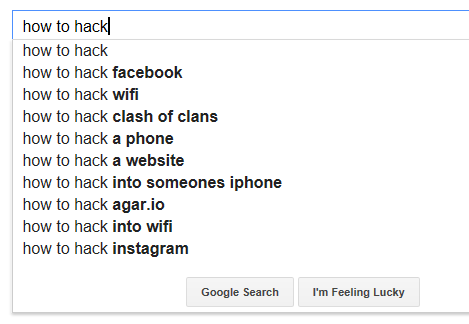
Agreed, this information is not overly useful. These hacks are basically on the opposite end of the threat scale from the over-hyped "Advanced Persistent Threat" (APT). Let's call it the "Basic Sporadic Annoyance" (BSA), just to come up with a new acronym :).
The BSAs still tell us though what "average" wannabe hackers seem to be interested in breaking into, namely: websites, online games, wifi and phones. Cars, pacemakers, fridges and power plants are not on the list, suggesting that these targets are apparently not yet "popular" enough.
Being fully aware of the "filter bubble" https://en.wikipedia.org/wiki/Filter_bubble we had several people try the same search, and they largely got the same result. Looks like Facebook really IS currently the main wannabe hacker target. But Facebook don't need to worry all that much. Because if you just type "How to h", then the suggestions reveal that other problems are even more prominent than "hacking Facebook":
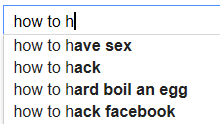
If your results (of the "how to hack" query, not the latter one) differ significantly, please share in the comments below. Updated to add: Thanks, we have enough samples now :)
Encryption of "data at rest" in servers
Over in the SANS ISC discussion forum, a couple of readers have started a good discussion https://isc.sans.edu/forums/Encryption+at+rest+what+am+I+missing/959 about which threats we actually aim to mitigate if we follow the HIPAA/HITECH (and other) recommendations to encrypt "data at rest" that is stored on a server in a data center. Yes, it helps against outright theft of the physical server, but - like many recent prominent data breaches suggest - it doesn't help all that much if the attacker comes in over the network and has acquired admin privileges, or if the attack exploits a SQL injection vulnerability in a web application.
There are types of encryption (mainly field or file level) that also can help against these eventualities, but they are usually more complicated and expensive, and not often applied. If you are interested in "data at rest" encryption for servers, please join the mentioned discussion in the Forum.
Gift card from Marriott?
Always nice when the spammers are so forthcoming to send their latest crud directly to our SANS ISC honeypot account. The current incarnation
Subject: Re: Your complimentary 3-night stay giftcard (Expires 09
From: "Marriott Gift Card" marriottgiftcard@summerallstar.review
came from
Received: from summerallstar.review (50.22.145.13-static.reverse.softlayer.com [50.22.145.13])
which kinda figures, Softlayer is among the cloud computing providers whose "get a virtual server FREE for one month" is an offering that scammers can't resist. The "Marriott" email said:
Marriott Special Gift Card:
=======================================================
Expires 09/15/15
Notification: #2595319
=======================================================
ALERT: Your Marriott-Gift Card will expire 09/15/15.
Please claim your gift-card at the link below:
http://seespecial.summerallstar[dot]review
This gift-card is only good for one-person to claim
at once with participation required. Please respect the
rules of the special-giftpromo.
=======================================================
Expires 09/15/15
Notification: #2595319
=======================================================
End-GiftCard Notification
.review ? How lovely! Let's use the opportunity to again *thank* ICANN for their moronic money grab, and all the shiny new useless "top level domains" that honest users and corporations now have to avoid and block. The lesson learned a couple years ago, when ".biz" and ".info" came online, should have been enough to know that the new cyber real estate would primarily get occupied by crooks. But here we are. I guess ICANN and most domain name pimps don't mind where their revenue stream comes from. But I digress.
Clicking on the link results in a rather unimaginative website, hosted on http://lucky-survey.com-hu3[dot]info, shown on the picture below.
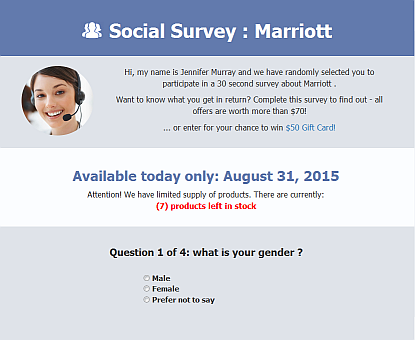
It doesn't (seem to - as far as I could tell) push any malware, but asks a couple of dumb questions, and then offers a prize. Ahem. Sort of a prize:
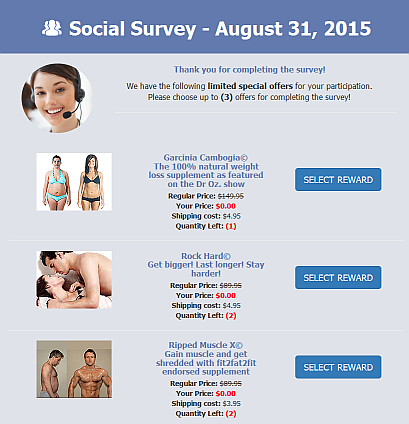
Somewhere along the way, it seems like the connection to "Marriott" got lost. Which is maybe all the better...

Comments