Exploit Kit Evolution - Neutrino
This is a guest diary submitted by Brad Duncan.
In September 2014 after the Neutrino exploit kit (EK) had disappeared for 6 months, it reappeared in a different form. It was first identified as Job314 or Alter EK before Kafeine revealed in November 2014 this traffic was a reboot of Neutrino [1].
This Storm Center diary examines Neutrino EK traffic patterns since it first appeared in the Spring of 2013.
Neutrino EK: 2013 through early 2014
Neutrino was first reported in March 2013 by Kafeine on his Malware Don't need Coffee blog [2]. It was also reported by other sources, like Trend Micro [3].
Here's a sample of Neutrino EK from April 2013 using HTTP over port 80:
Shown above: Neutrino EK traffic from April 2013.
By the summer of 2013, we saw Neutrino use HTTP over port 8000, and the traffic patterns had evolved. Here's an example from June 2013, back when I first started blogging about malware traffic [4]:
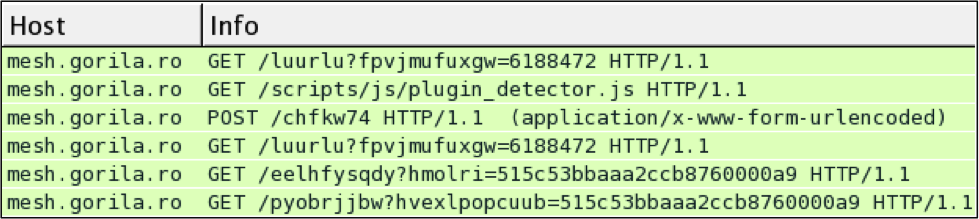
Shown above: Neutrino EK traffic from June 18th, 2013.
In October 2013, Operation Windigo (an on-going operation that has compromised thousands of servers since 2011) switched from using the Blackhole EK to Neutrino [5].
Before Neutrino EK disappeared in March of 2014, I usually found it in traffic associated with Operation Windigo. Here are two examples from February and March 2014 [6] [7]:
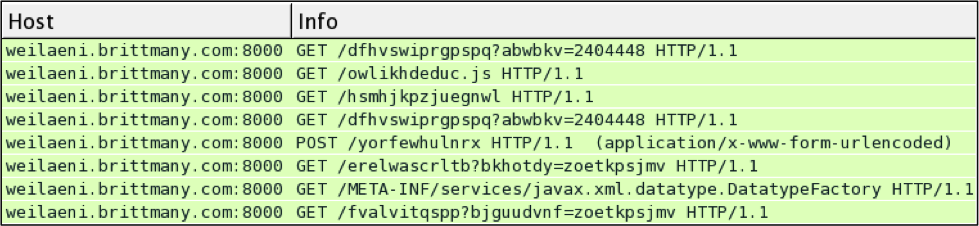
Shown above: Neutrino EK traffic from February 2nd, 2014.
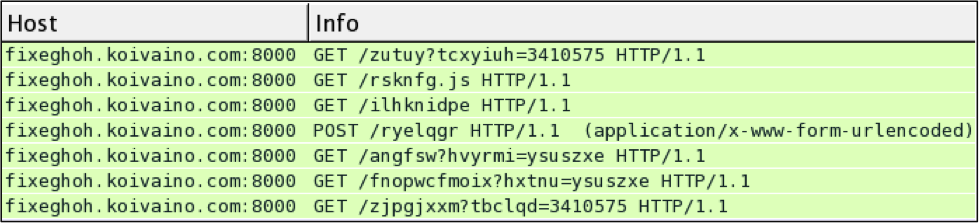
Shown above: Neutrino EK traffic from March 8th, 2014.
March 2014 saw some reports about the EK's author selling Neutrino [8]. Later that month, Neutrino disappeared. We stopped seeing any sort of traffic or alerts on this EK.
Neutrino EK since December 2014
After Kafeine made his announcement and EmergingThreats released new signatures for this EK, I was able to infect a few VMs. Here's an example from November 2014 [9]:
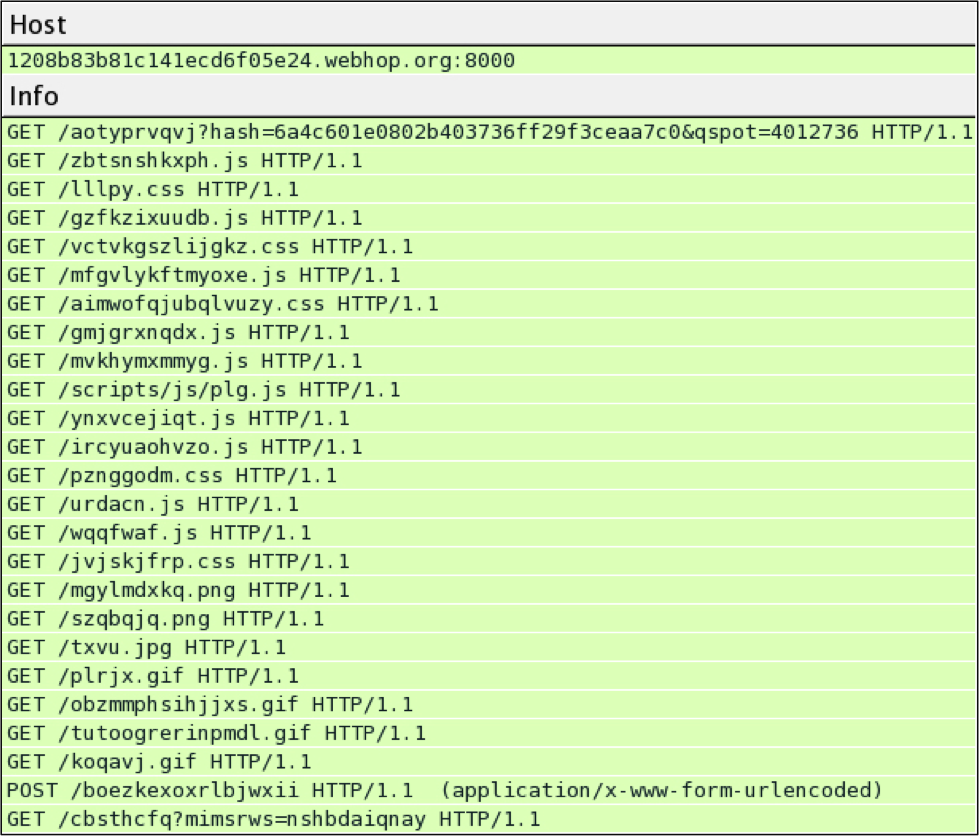
Shown above: Neutrino EK traffic from November 29th, 2014.
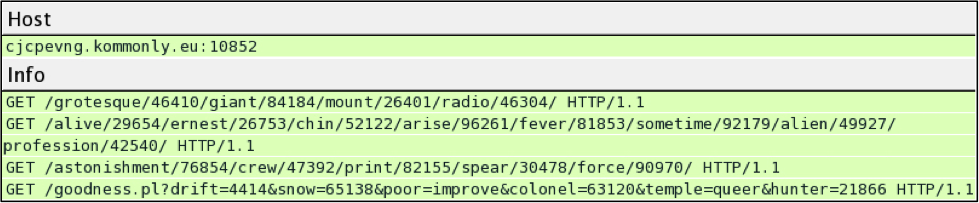
Traffic patterns have remained relatively consistent since Neutrino reappeared. I infected a VM on February 2nd, 2015 using this EK. Below are the HTTP requests and responses to Neutrino EK on vupwmy.dout2.eu:12998.
- GET /hall/79249/card/81326/aspect/sport/clear/16750/mercy/flash/clutch/1760/
absorb/43160/conversation/universal/ - HTTP/1.1 200 OK (text/html) - Landing page
- GET /choice/34831/mighty/drift/hopeful/19742/fantastic/petunia/fine/12676/
background/76767/seal/74018/street/20328/ - HTTP/1.1 200 OK (application/x-shockwave-flash) - Flash exploit
- GET /nowhere/44312/clad/29915/bewilder/career/pass/sinister/
- HTTP/1.1 200 OK (text/html) - No actual text, about 25 to 30 bytes of data, shows up as "Malformed Packet" in Wireshark.
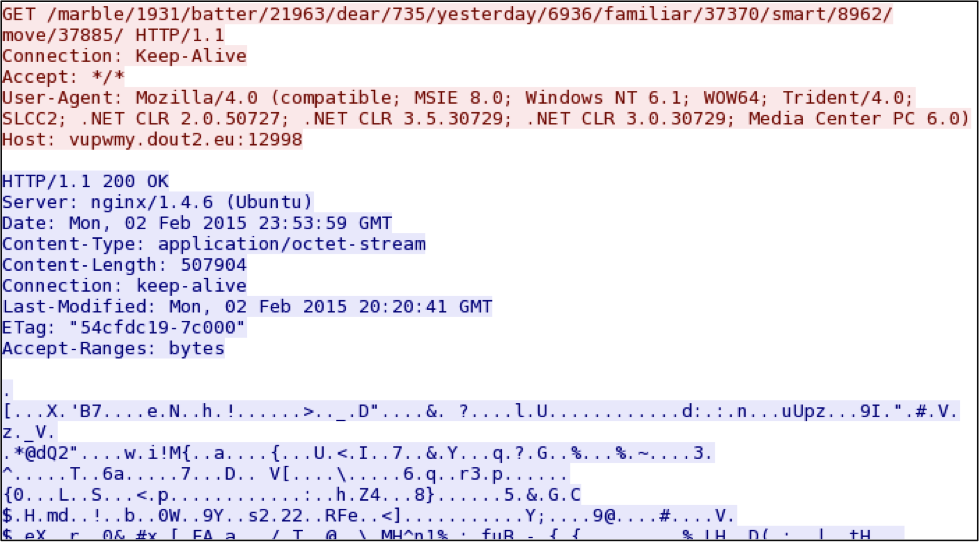
- GET /marble/1931/batter/21963/dear/735/yesterday/6936/familiar/37370/
- smart/8962/move/37885/
- HTTP/1.1 200 OK (application/octet-stream) - Encrypted malware payload
- GET /lord.phtml?horror=64439&push=75359&pursuit=wash&fond=monsieur&
wooden=forever&content=21179&despite=liberty&stalk=shiver&faithful=10081&
bold=35942 - HTTP/1.1 404 Not Found OK (text/html)
- GET /america/86960/seven/quiet/blur/belong/traveller/12743/gigantic/96057/
trunk/69375/await/30077/cunning/39832/betray/638/ - HTTP/1.1 404 Not Found OK (text/html)
The malware payload sent by the EK is encrypted.
Shown above: Neutrino EK sends the malware payload.
I extracted the malware payload from the infected VM. If you're registered with Malwr.com, you can get a copy from:
https://malwr.com/analysis/NjFjNjQyYjBkMzVhNGE4MWE4Mjc1Mzk2NmQxNjFjM2E/
This malware is similar to previous Vawtrak samples I've seen from Neutrino and Nuclear EK last month [10] [11].
Closing Thoughts
Exploit kits tend to evolve over time. You might not realize how much the EK has changed until you look back through the traffic. Neutrino EK is no exception. It evolved since it first appeared in 2013, and it significantly changed after reappearing in December 2014. It will continue to evolve, and many of us will continue to track those changes.
----------
Brad Duncan is a Security Researcher at Rackspace, and he runs a blog on malware traffic analysis at http://www.malware-traffic-analysis.net
References:
[1] http://malware.dontneedcoffee.com/2014/11/neutrino-come-back.html
[2] http://malware.dontneedcoffee.com/2013/03/hello-neutrino-just-one-more-exploit-kit.html
[3] http://blog.trendmicro.com/trendlabs-security-intelligence/a-new-exploit-kit-in-neutrino/
[4] http://malware-traffic-analysis.net/2013/06/18/index.html
[5] http://www.welivesecurity.com/wp-content/uploads/2014/03/operation_windigo.pdf
[6] http://malware-traffic-analysis.net/2014/02/02/index.html
[7] http://malware-traffic-analysis.net/2014/03/08/index.html
[9] http://www.malware-traffic-analysis.net/2014/12/01/index.html
[10] http://malware-traffic-analysis.net/2015/01/26/index.html
[11] http://www.malware-traffic-analysis.net/2015/01/29/index.html

Comments